Free setup! Speak with us anytime: 480-624-2500
What is Phishing?
Phishing is a scheme where hackers get users to hand over sensitive information, like passwords and social security numbers. It typically involves sending spam email that looks like it's coming from a trusted source, like a bank (this is the bait), that then links to a fraudulent website impersonating the trusted source (this is the trap). The unsuspecting target then enters the information the attacker's looking for, thinking he's actually on a Website he trusts.
Understanding what these attacks look like and how they work can help you spot phishing attempts, as well as give you some information about what to do if your website has been compromised to host a phishing trap.
Phishing Email (Bait)
Phishing emails impersonate trustworthy organization to steal users' credentials. In the example below, the email employs a common phishing practice: asking users to update their account information. However, when you hover over the link, it doesn't lead to the company's actual website — it leads to a phishing trap Website instead:
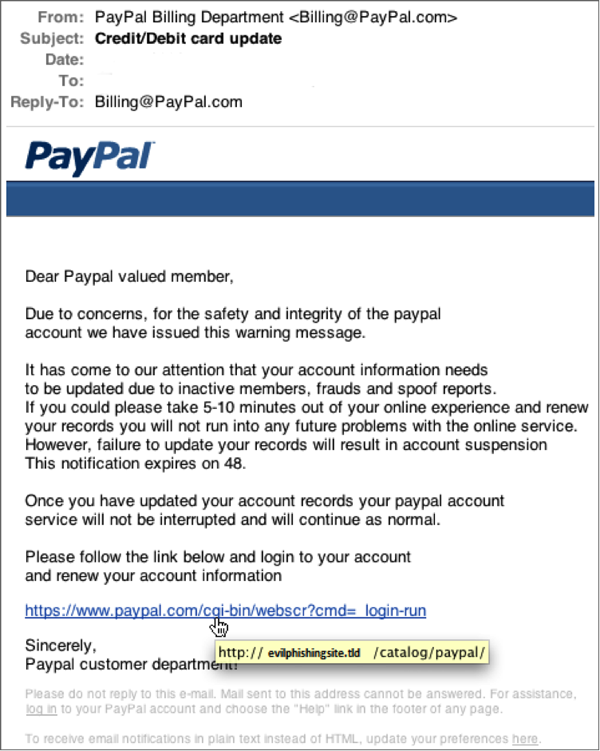
Phishing Website (Trap)
Once users click the link in a phishing email, they're brought a fraudulent website that the attacker's impersonating. This trap Website asks users to enter some kind of sensitive information, like a username or banking information. Once the user enters the information, it's sent to the hacker who uses it to compromise the user's account.
Here's an example of a convincing phishing page:
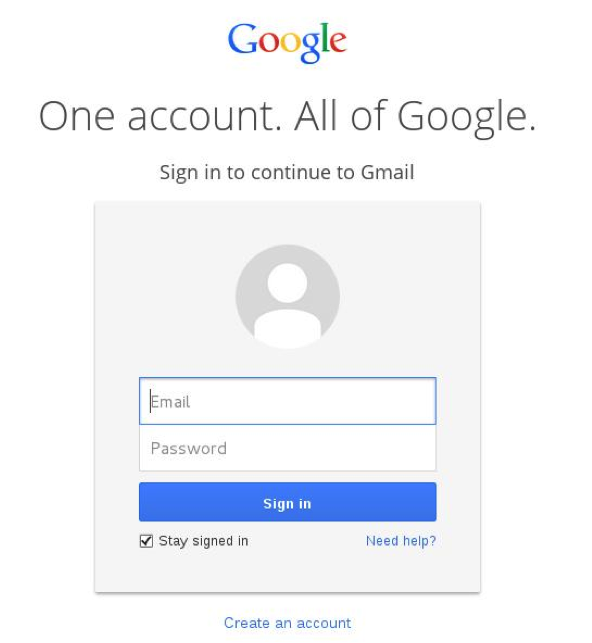
The only way to tell this isn't the actual Google® login page is to look at the browser's address bar. If you look just to the left of the first forward slash after the ones in http://, you'll notice the domain name is definitely not going to be google.com.
For example, in http://login.google.com.evilphishingsite.com/index.html, the Website you're actually on is actually evilphishingsite.com.
Phishing Websites Hosted on Your Account
If your Website suffers an FTP compromise, hackers might use your account to host a phishing website. We have more information about that in What is an FTP compromise?
When you view your files and directories, you can be sure that the directories named after well-known businesses (such as banks or Google) are being used for phishing. For example:
- ./html/HSBC/hsbc.com/
- ./html/Gmail/googledocs/Googledock/
More Information
Because of phishing's prevalence, there's a lot of information about it available. Check out the following resources for more information about it and how to protect yourself from it:
Domain Registration
Pay less for website domain names. Register your own .com, .net or .org for as low as $10.18 per year. We have everything you need to get online with your new domain.Website Builder
For as little as $3.89 per month you can build your Website online with Website Builder using our easy to use professional templates. Play Video - Demo
Quick Shopping Cart
Build and run your own successful online store in minutes. You're just five easy steps away! Shopping Cart works with Google® and eBay® Play Video
Website Hosting
Everything needed to give your website the high-performance home it deserves. Protect transactions and secure your customer's data with a SSL Certificate
